Over 80% of breaches originate from outside the network1. Attackers are gaining access through phishing, ransomware, and point-of-sale hacking. Once in, they command and control across your network boundaries.
Forensic data collection, including network forensics, is an essential element for your incident response capabilities.
What is network forensics?
Network forensics is a sub-branch of digital forensics. It involves monitoring and analysis of computer traffic for the purposes of intrusion detection, legal evidence, or information gathering.
Collecting forensic data for incident response
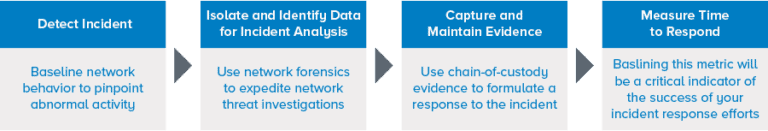
Before you can identify a threat, you must be able to see evidence of the attack within your IT environment.
- To truly understand an incident, you need aggregate packet capture and the derived metadata for quick access to pertinent network forensics details.
- Once your team is effectively collecting security and log data, forensic sensors can provide even deeper and broader visibility.
- Network forensic sensors will fill gaps in visibility when logs are insufficient.
- Mean time to respond (MTTR) is your team’s critical metric to determine if your forensic data is improving your incident response efforts.
Start collecting forensic data from your network
Transform your physical or virtual system into a network forensics sensor for free with NetMon Freemium.
Evaluating your network forensics capabilities
LogRhythm NetMon can help you detect, identify, and capture the forensic evidence you need to reduce your incident response time. When combined with the LogRhythm NextGen SIEM Platform, NetMon correlates data with additional sources, provides analytics to identify patterns, and manages an incident through to case management.
To understand if you are using network forensics successfully, ask yourself the following questions:
- Am I capturing the appropriate level of detail to understand if I have real incidents that require investigations?
- Can I find the evidence I need to investigate incidents?
- Can I extract and maintain sufficient evidence to formulate a response?
LogRhythm NetMon for network forensics
Detect
- Real-time monitoring and big data analytics
- Dashboards to identify threats
- Easy searches with rich, session-based metadata
- Out-of-band architecture
Identify
- Application recognition of over 3,000 distinct applications with rich classification and extensive metadata for visibility into network sessions
- Access to rich forensic data
- Script-based deep packet analytics (DPA) for real-time detection
Capture
- Session-based full packet capture
- Layer 4–7 analysis with true application ID and rich metadata
- SmartCapture™ selective packet capture for cost efficiency
- SmartResponse™ automation actions to obtain sessions through packet capture and future case analysis
Detect and respond to network-borne threats in real time
Go beyond limited network traffic analysis. With advanced analytics and embedded SOAR technology, LogRhythm NDR helps your security team work faster than ever before.
Breaking down the cost and complexity to network monitoring
Network monitoring, network forensics, and traffic analytics technology enable faster threat detection and incident response. But only a fraction of enterprises deploys this technology today.
In this on-demand webcast, you’ll learn how to break down the complexity of network monitoring tools and review scenarios using network analysis in a forensics investigation.
