Organizations generate massive amounts of data across various log sources. Without proper monitoring tools, how do you know what activity is legitimate versus a potential cyberthreat?
To enable real-time insight into security events across your environment, you need a log management solution. Learn how LogRhythm can address your observability and compliance needs by consulting with an expert one-on-one.

Benefits of Log Management Solutions
Gain Greater Visibility
Eliminate visibility gaps and see the full picture of what is happening across your users, data, and systems.
Understand Your Data
Know what activity is normal versus malicious by analyzing your data through contextualization and enrichment.
Achieve Compliance
Abide by necessary cybersecurity compliance standards and easily audit log data and automate reports.
How LogRhythm Helps with Log Management
When choosing a log management solution, there are a variety of features and capabilities to look for. Here’s how LogRhythm can help you collect, enrich, and analyze log data.
Log Collection and Customization
Collect from devices, applications, and sensors in your environment. LogRhythm offers out-of-the-box support to quickly ingest log sources that are crucial for your organization. We also help you ingest custom log sources, ensuring that all network log data is collected and analyzed.
Advanced Search Capabilities
Leverage keyword driven search and suggested search features to easily sift through all the noise within your environment. LogRhythm’s graphical user interface and search experience makes it easy to search through mass amounts of log data.
Correlating and Enriching Log Data
Choose from preconfigured, out-of-the-box correlation rule sets or customize rules. With deep intelligence into unique data source types and pre-built processing rules, LogRhythm’s Machine Data Intelligence (MDI) Fabric can parse and infer searchable metadata fields.
Scalability and Flexibility
Get flexible deployment options depending on your organization’s needs. LogRhythm supports cloud and on-prem infrastructures to expand quickly, and continue to perform at any scale — all while minimizing the impact to your ongoing operations.
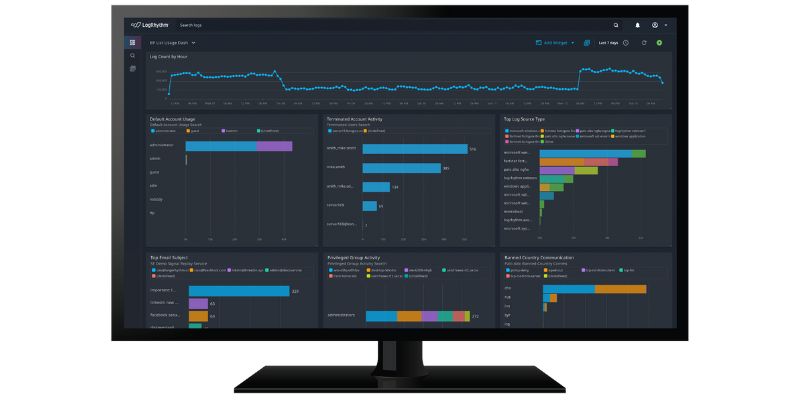
Visualizations and Dashboards
Analysts need a quick snapshot of what is happening in the environment to easily drill down. LogRhythm enables you to create custom dashboards that are easy to digest and tailored to your unique needs.
LogRhythm’s Log Management Platforms
Depending on your business requirements, we have flexible options to deploy in self-hosted or cloud environments.
LogRhythm SIEM: Self-Hosted SIEM
With high-performance analytics, enhanced log collection, and a seamless incident response workflow, LogRhythm SIEM helps your organization uncover threats, mitigate attacks, and comply with necessary mandates.

LogRhythm Axon: Cloud-Native SIEM
Leverage powerful security analytics and automatic log
collection and enrichment to easily identify, analyze, and report on potential threats. LogRhythm Axon provides automatic visibility into SaaS, self-hosted cloud, and on-prem environments.
Recommended Log Management Resources
Get Started With Log Management
Log management solutions help security teams gain visibility across the environment. Learn how LogRhythm can enable your team to search through log data and respond to security incidents faster than ever before.


