Regulatory compliance is a necessary, but often complicated and expensive component of modern business. Keeping up with compliance and reporting requirements may seem like daunting tasks when you’re strapped for security resources. That’s where LogRhythm can help.
LogRhythm SIEM provides holistic visibility into your network and improves detection and response capabilities. Paired with LogRhythm’s compliance automation modules, your team can comply with necessary mandates more efficiently and effectively than previous manual processes. Our in-house LogRhythm Labs compliance experts develop and maintain these modules, providing you with prebuilt content specifically mapped to the individual controls of each regulation.
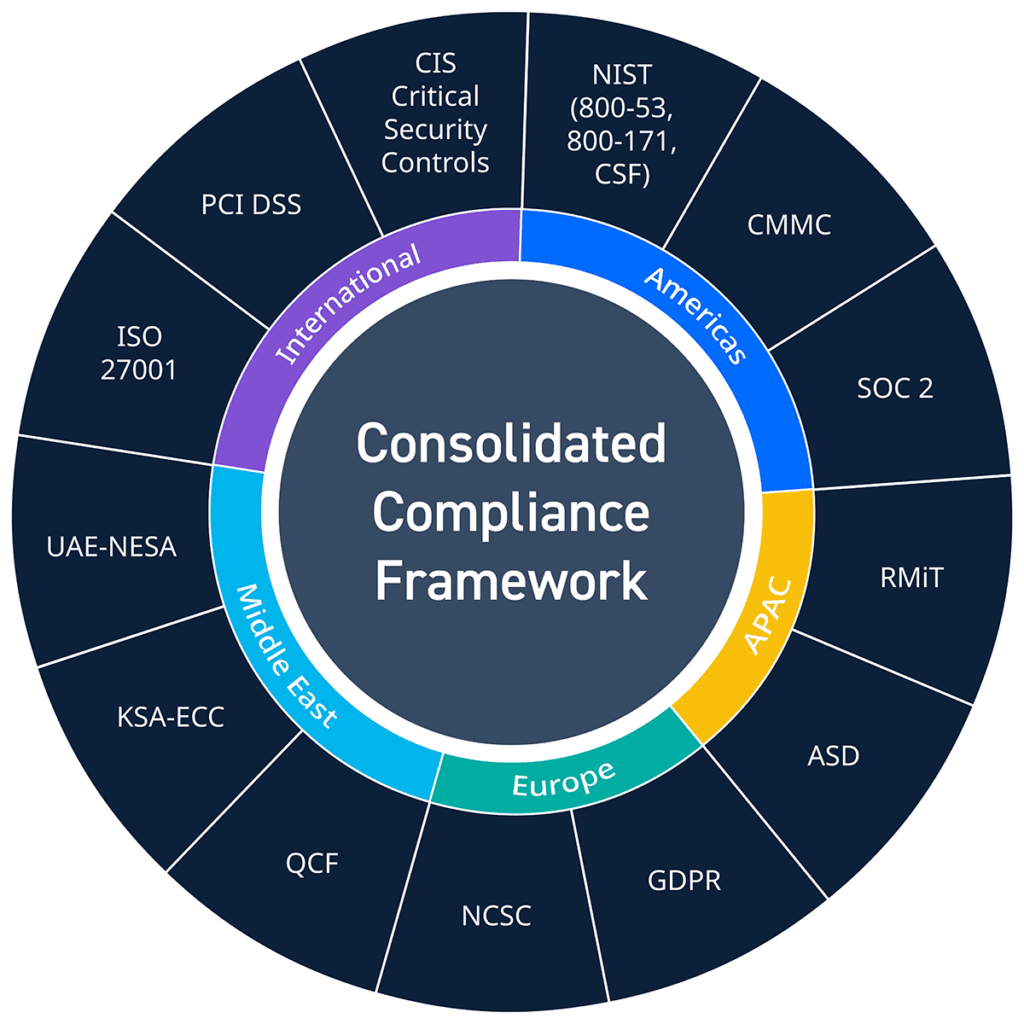
Our Consolidated Compliance Framework further simplifies your compliance program by providing a core, shared module mapped to dozens of regulations, encompassing the majority of common cybersecurity controls. This reduces the effort spent on setup and correlating multiple, identical alarms across frameworks.
With LogRhythm compliance automation modules, you’ll be able to:
- Reduce the burden of assuring and demonstrating regulatory compliance
- Easily deploy prebuilt reports for audit and management review
- Detect compliance violations automatically and in real time
201 CMR 17.00
To ensure compliance with 201 CMR 17 requirements, information systems and applications are monitored in real time. AI Engine rules, alarms, reports, and more help your team comply quickly and easily.
Australian Signals Directorate (ASD)
The Australian Signals Directorate (ASD) provides help and guidance for organizations keen to improve and maintain their cyber readiness.
BSI: IT Grundschutz
LogRhythm’s BSI: IT Fundamentals Compliance Module provides predefined alarms, reports, and lists to enable a quick and easy implementation of the BSI IT-Grundschutz catalogs.
CIS Critical Security Controls
The Center for Internet Security (CIS) has developed the top 20 Critical Security Controls (CSC) to help IT professionals protect their environment against both external and internal attacks.
DoDi 8500.2
To ensure compliance with 201 CMR 17 requirements, information systems and applications are monitored in real time. AI Engine rules, alarms, reports, and more help your team comply quickly and easily.
FISMA
LogRhythm’s FISMA compliance module aligns your organization’s risk assessment with forensic investigations, reporting, and prioritization settings — implementing controls for systems that support operations and assets.
GDPR
Learn how LogRhythm’s GDPR Compliance Module addresses 16 technology-focused GDPR Articles through prebuilt content, including rules, alerts, and reports.
GLBA
Address GLBA requirements regarding financial privacy, safeguards, and pretexting through central monitoring of activity and conditions. Collect log data from hosts, applications, network devices, and more.
GPG 13
Directly address control obligations mandated in GPG 13 with LogRhythm’s report packages, AI Engine rules, investigations, and tails. With optimized indexing structure, you’ll apply real-time analytics to expose areas of non-compliance.
HIPAA
Through advanced correlation rules and machine learning, LogRhythm’s prebuilt Health Care Compliance Automation Module provides a comprehensive security framework that protects your patients and improves security posture.
ISO 27001
The collection, management, and analysis of log data are integral when following ISO 27001 guidelines. With LogRhythm’s powerful compliance correlation and alerting, you’ll identify critical issues and meet reporting requirements.
KSA-ECC
LogRhythm has released new compliance use cases and predefined reports to enable organizations to better comply with the Kingdom of Saudi Arabia (KSA) Essential Cybersecurity Controls (ECC).
MAS-TRMG
As a component of LogRhythm’s unified security platform, the LogRhythm MAS-TRMG Compliance Automation Module helps FIs comply with Singapore business guidelines through 24x7 monitoring and real-time alerting.
NEI 08-09 Rev 6
LogRhythm’s entirely automated process of collecting and retaining audit logs gives you quick insight for regulatory control, accountability, incident response, and system and information integrity.
NERC CIP
To help you meet NERC CIP compliance mandates, LogRhythm’s automation module streamlines the compliance process, providing advanced features for monitoring and enforcement to deliver content through reporting packages.
NIST 800-53
NIST 800-53 reporting packages from LogRhythm ensure you’re meeting reporting mandate requirements by categorizing, identifying, and normalizing all of your log data for easy analysis and reporting.
NIST Cybersecurity Framework
With LogRhythm’s NIST Cybersecurity Framework compliance platform, log collection, archiving, and recovery are fully automated across the entire IT infrastructure as a prebuilt feature.
NRC Regulatory Guide 57.1
LogRhythm’s NRC RG 5.71 compliance for nuclear facilities provides high assurance that digital computer and communication systems and networks are adequately protected against cyberattacks.
NYDFS Cybersecurity Compliance Regulation
Learn about the latest NYDFS Cybersecurity regulations, and how the LogRhythm SIEM platform helps your organization meet compliance regulations.
PCI DSS
LogRhythm’s PCI DSS compliance module simplifies investigations through alarms and reports that are automatically associated with accurate asset categories, providing immediate notification of activities that impact your systems.
Risk Management in Technology (RMiT)
The LogRhythm SIEM platform enables your organization to meet many RMiT guidelines by collecting, managing, and analyzing log data.
SOX
LogRhythm’s preconfigured reporting packages improve your organization’s security and SOX compliance posture while reducing costs through AI Engine rules and alerts, prebuilt dashboards, and a robust SOX reporting package.
SWIFT
Learn how LogRhythm helps your organization comply with the SWIFT Customer Security Controls Framework and take an integrated, multipronged approach to securing your financial transactions.
UAE-NESA
LogRhythm’s UAE-NESA Compliance Automation Suite provides pre-packaged content that is associated with UAE-NESA asset categories, easing compliance concerns.
Optimize your SOC efficiency with LogRhythm
Watch the demo to see the LogRhythm SIEM platform in action.
LogRhythm’s Built-in Playbooks Optimize the Efficiency of your SOC
This demo shows you how the built-in playbooks help your team with collaboration, guided case workflow and executable best practices.